SHAttered – SHA-1 is definitely dead
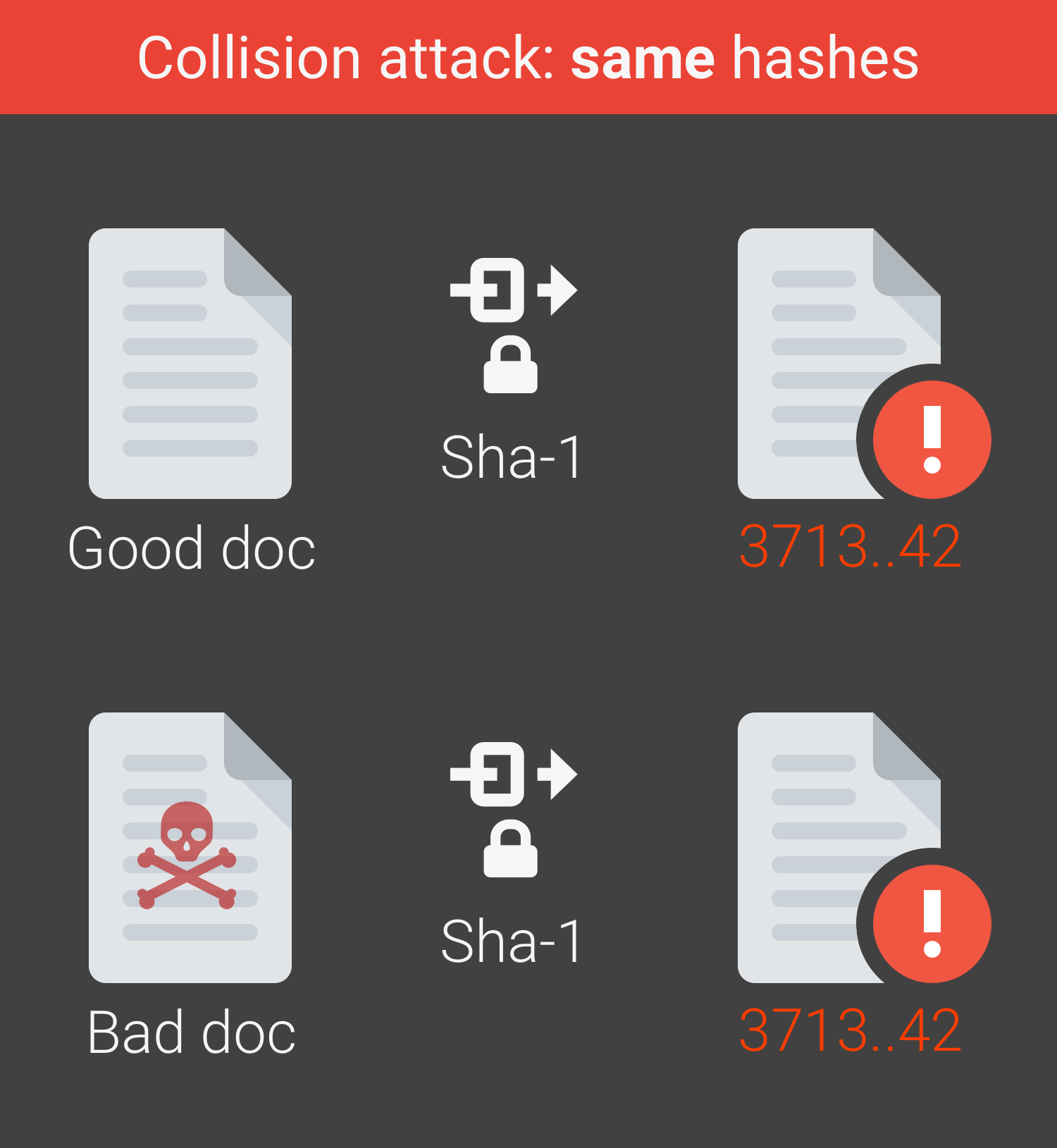
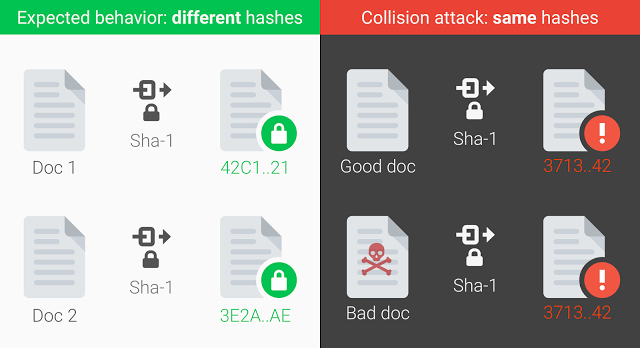
SHA-1 was introduced in 1995 and, in 2015, researchers disclosed a method that lowered the cost of an SHA-1 collision to $75,000-$120,000 using Amazon’s EC2 cloud over a period of a few months. Despite steps taken by major companies to move away from SHA-1, the hash function is still widely used. Now researchers at Google have realized the first real world collision attack against SHA-1, creating two documents with different content but identical hashes.
In cryptography, SHA-1 (Secure Hash Algorithm 1) is a cryptographic hash function designed by the United States National Security Agency and is a U.S. Federal Information Processing Standard published by the United States NIST. SHA-1 produces a 160-bit (20-byte) hash value known as a message digest. A SHA-1 hash value is typically rendered as a hexadecimal number, 40 digits long.
This technique has been dubbed “SHA-1 shattered” or “SHAttered”:
Today, 10 years after of SHA-1 was first introduced, we are announcing the first practical technique for generating a collision. This represents the culmination of two years of research that sprung from a collaboration between the CWI Institute in Amsterdam and Google.
Q&A
Who is capable of mounting this attack?
This attack required over 9,223,372,036,854,775,808 SHA1 computations. This took the equivalent processing power as 6,500 years of single-CPU computations and 110 years of single-GPU computations.
How does this attack compare to the brute force one?
The SHAttered attack is 100,000 faster than the brute force attack that relies on the birthday paradox. The brute force attack would require 12,000,000 GPU years to complete, and it is therefore impractical.
Isn’t SHA-1 deprecated?
Today, many applications still rely on SHA-1, even though theoretical attacks have been known since 2005, and SHA-1 was officially deprecated by NIST in 2011. We hope our practical attack on SHA-1 will increase awareness and convince the industry to quickly move to safer alteratives, such as SHA-256.
How can I protect myself?
You can use file tester to check your files. If you use Chrome, you will be automatically protected from insecure TLS/SSL certificates, and Firefox has quickly reacted to this announcement, and deprecated SHA-1 as of February 24th, 2017. Files sent via Gmail or saved in Google Drive are already automatically tested against this attack.
What types of systems are affected?
Any application that relies on SHA-1 for digital signatures, file integrity, or file identification is potentially vulnerable. These include:
- Digital Certificate signatures
- Email PGP/GPG signatures
- Software vendor signatures
- Software updates
- ISO checksums
- Backup systems
- Deduplication systems
- GIT
…
How do I patch/upgrade my system?
Consider using safer alternatives, such as SHA-256, or SHA-3.
More technical information are available on the dedicated site, shattered.it:
source: https://andreafortuna.org, https://shattered.it/